Do you use the dig command to make DNS queries? You can use curl for the same thing, and you do not need dig anymore. It also runs over HTTPS and is a lot more secure.
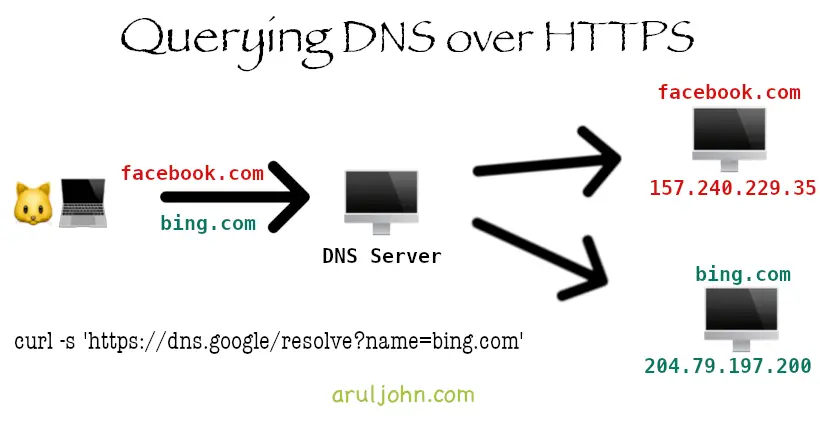
Table of Contents
- What is the dig command?
- How do we query the traditional way?
- What is DNS over HTTP?
- Mozilla Firefox uses DoH for American users
- How do we query DNS over HTTP using Google's DNS server?
- How to query for AAAA records using Google's DoH
- How to query for AAAA records using Cloudflare's DoH
- List of DNS-over-HTTPS DoH servers
- DoH status codes
- DoH boolean keys
- Conclusion
What is the dig command?
dig stands for Domain Information Groper, and is used mainly to get DNS information as well as troubleshoot DNS issues. DNS stands for Domain Name System, and stores information related to domain names as a distributed database. Think of DNS like an address book where you translate domain names into IP addresses.
When we want to find the IP addresses associated with a hostname, we query the DNS using the dig command.
How do we query the traditional way?
Let us query a DNS server for the domain slashdot.org.
$ dig slashdot.org
; <<>> DiG 9.10.6 <<>> slashdot.org
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 31812
;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 512
;; QUESTION SECTION:
;slashdot.org. IN A
;; ANSWER SECTION:
slashdot.org. 300 IN A 104.18.36.64
slashdot.org. 300 IN A 172.64.151.192
;; Query time: 40 msec
;; SERVER: 192.168.1.1#53(192.168.1.1)
;; WHEN: Sun Mar 10 17:39:10 EDT 2024
;; MSG SIZE rcvd: 73
As we can see, in the HEADER section, there are two entries for the ANSWER section:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 31812
;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
In the ANSWER section, there are two IP addresses related to the A address record, and they are 104.18.36.64 and 172.64.151.192.
;; ANSWER SECTION:
slashdot.org. 300 IN A 104.18.36.64
slashdot.org. 300 IN A 172.64.151.192
If we want only the IP addresses and not the extra information, we do this:
$ dig +short slashdot.org
104.18.36.64
172.64.151.192
Using Google's DNS servers
Google has two public DNS servers and 8.8.8.8 and 8.8.4.4. If we want to do a DNS query against Google's DNS server 8.8.8.8, we append @8.8.8.8 after the dig command like this:
$ dig @8.8.8.8 +short slashdot.org
104.18.36.64
172.64.151.192
Google's DNS usually has faster response times. Also, reliability is better with Google's DNS than the default ISP's DNS servers. I noticed that Google's DNS response time was much faster than Comcast's and Verizon's DNS servers.
What is DNS over HTTP?
Using dig, the DNS query is unencrypted, and the request and response are both unencrypted. By intercepting and this, a malicious user can A malicious user can redirect you to a different destination, like a fake credit card or bank website. This is called a Man-in-the-Middle attack (MITM).
When you use a free public Wi-Fi service, which can be lax in terms of security or performance, you are vulnerable to MITM attacks while on their networks.
DNS Over HTTPS entered the chat
DNS over HTTPS or DOH is an updated and secure way to query DNS servers over the HTTPS protocol. Using DoH, DNS queries are processed by a third party DoH provider and bypass the local resolver. Both the requests and responses are encrypted.
While querying using DoH, you ride on HTTPS with the query between your machine and the DNS server or resolver.
Using DoH, if you use a public Wi-Fi service to query DNS, the security is improved a lot and the traffic appears like regular HTTPS traffic.
The DNS over HTTPS protocol was written in RFC 8484. You can read more there.
Mozilla Firefox uses DoH for American users
For the last 4 years, the Mozilla Firefox browser has enabled DoH for American users by default. DNS queries are automatically encrypted using DoH.
How do we query DNS over HTTP using Google's DNS server?
Using curl, we can query slashdot.org against multiple DoH servers using JSON API.
We will query against Google's DNS server. For this, we
1) send the JSON request header Accept: application/dns-json
2) query against the endpoint https://dns.google/resolve
3) use query parameter name with that endpoint
We get a JSON response.
curl -H 'Accept: application/dns-json' 'https://dns.google/resolve?name=slashdot.org'
{"Status":0,"TC":false,"RD":true,"RA":true,"AD":false,"CD":false,"Question":[{"name":"slashdot.org.","type":1}],"Answer":[{"name":"slashdot.org.","type":1,"TTL":300,"data":"172.64.151.192"},{"name":"slashdot.org.","type":1,"TTL":300,"data":"104.18.36.64"}],"Comment":"Response from 46.31.236.1."}
This is the prettified output:
{
"Status": 0,
"TC": false,
"RD": true,
"RA": true,
"AD": false,
"CD": false,
"Question": [
{
"name": "slashdot.org.",
"type": 1
}
],
"Answer": [
{
"name": "slashdot.org.",
"type": 1,
"TTL": 300,
"data": "172.64.151.192"
},
{
"name": "slashdot.org.",
"type": 1,
"TTL": 300,
"data": "104.18.36.64"
}
],
"Comment": "Response from 46.31.236.1."
}
The output is exactly the same as the traditional DNS query, except that it is in JSON format.
If you want to use the jq tool to get just the IP addresses, you can do this:
$ curl -s 'https://dns.google/resolve?name=slashdot.org' | jq -r '.Answer[] | .data'
172.64.151.192
104.18.36.64
How to query for AAAA records using Google's DoH
If you want to get all the AAAA records for domain name bing.com using DoH, add the type query parameter. I am adding | jq to prettify it.
$ curl -s 'https://dns.google/resolve?name=bing.com&type=AAAA' | jq
{
"Status": 0,
"TC": false,
"RD": true,
"RA": true,
"AD": false,
"CD": false,
"Question": [
{
"name": "bing.com.",
"type": 28
}
],
"Answer": [
{
"name": "bing.com.",
"type": 28,
"TTL": 2741,
"data": "2620:1ec:c11::200"
}
]
}
We found the IPv6 address of bing.com to be 2620:1ec:c11::200.
How to query for AAAA records using Cloudflare's DoH
Cloudflare has its own DNS over HTTP server. Using curl, we will query against Cloudflare's DNS server. For this, we
1) send the JSON request header Accept: application/dns-json
2) query against the endpoint https://cloudflare-dns.com/dns-query
3) use query parameter name with that endpoint
4) add the type query parameter with type=AAAA
$ curl -s -H 'Accept: application/dns-json' 'https://cloudflare-dns.com/dns-query?name=bing.com&type=AAAA' | jq
{
"Status": 0,
"TC": false,
"RD": true,
"RA": true,
"AD": false,
"CD": false,
"Question": [
{
"name": "bing.com",
"type": 28
}
],
"Answer": [
{
"name": "bing.com",
"type": 28,
"TTL": 3202,
"data": "2620:1ec:c11::200"
}
]
}
List of DNS-over-HTTPS DoH servers
Google and Cloudflare are one of many DoH servers. Here is a longer list.
| Provider | Endpoint | Documentation |
|---|---|---|
| https://dns.google/dns-query | https://developers.google.com/speed/public-dns/docs/doh/ | |
| Cloudflare | https://cloudflare-dns.com/dns-query | https://developers.cloudflare.com/1.1.1.1/dns-over-https/ |
| Mozilla Cloudflare | https://mozilla.cloudflare-dns.com/dns-query | https://developers.cloudflare.com/1.1.1.1/commitment-to-privacy/privacy-policy/firefox/ |
DoH status codes
In the JSON output, you will notice that Status has a value. These are the meanings of the Status values.
| Status Value | Meaning |
|---|---|
| 0 | NOERROR - Successful response for DNS query |
| 1 | FORMERROR - Invalid DNS query request format |
| 2 | SERVFAIL - DNS server failed to complete DNS request |
| 3 | NXDOMAIN - Domain name does not exist |
| 4 | NOTIMP - Function not implemented |
| 5 | REFUSED - DNS server refused to answer the query |
| 6 | YXDOMAIN - Name that should not exist does exist |
| 7 | XRRSET - RRset that should not exist does exist |
| 8 | NOTAUTH - DNS server not authoritative for the zone |
| 9 | NOTZONE - Name not in zone |
DoH boolean keys
In the JSON output, you will notice a bunch of keys along in the same level as Status. These are the meanings of those keys.
| Key | Meaning |
|---|---|
| TC | Truncated Response - Whether the response has been truncated due to size restrictions |
| RD | Recursion Desired - Whether the client requested recursive resolution |
| RA | Recursion Available - Whether the server supports recursive query support |
| AD | Authentic Data - Whether the response has been validated |
| CD | Checking Disabled - Whether the client has requested to disable validation |
You will find detailed explaination about the DNS Header Flags.
Conclusion
DNS-over-HTTPS is ongoing and a work in progress. Its adaptation continues to increase and at some point will phase out the dig utility. Personally, I like the JSON API and prefer it to the traditional dig utility. There are also tools such as dog that work with DoH directly.
Related Posts
If you have any questions, please contact me at arulbOsutkNiqlzziyties@gNqmaizl.bkcom. You can also post questions in our Facebook group. Thank you.